AWS Security Groups
Introduction
In the realm of cloud security, AWS Security Groups play a crucial role in controlling network access to your resources within an Amazon Virtual Private Cloud (VPC). Understanding the stateful nature of these security groups is vital for managing and configuring network security effectively. This guide will delve into how AWS Security Groups work, their stateful characteristics, and provide practical examples and best practices for their management.
What Are AWS Security Groups?
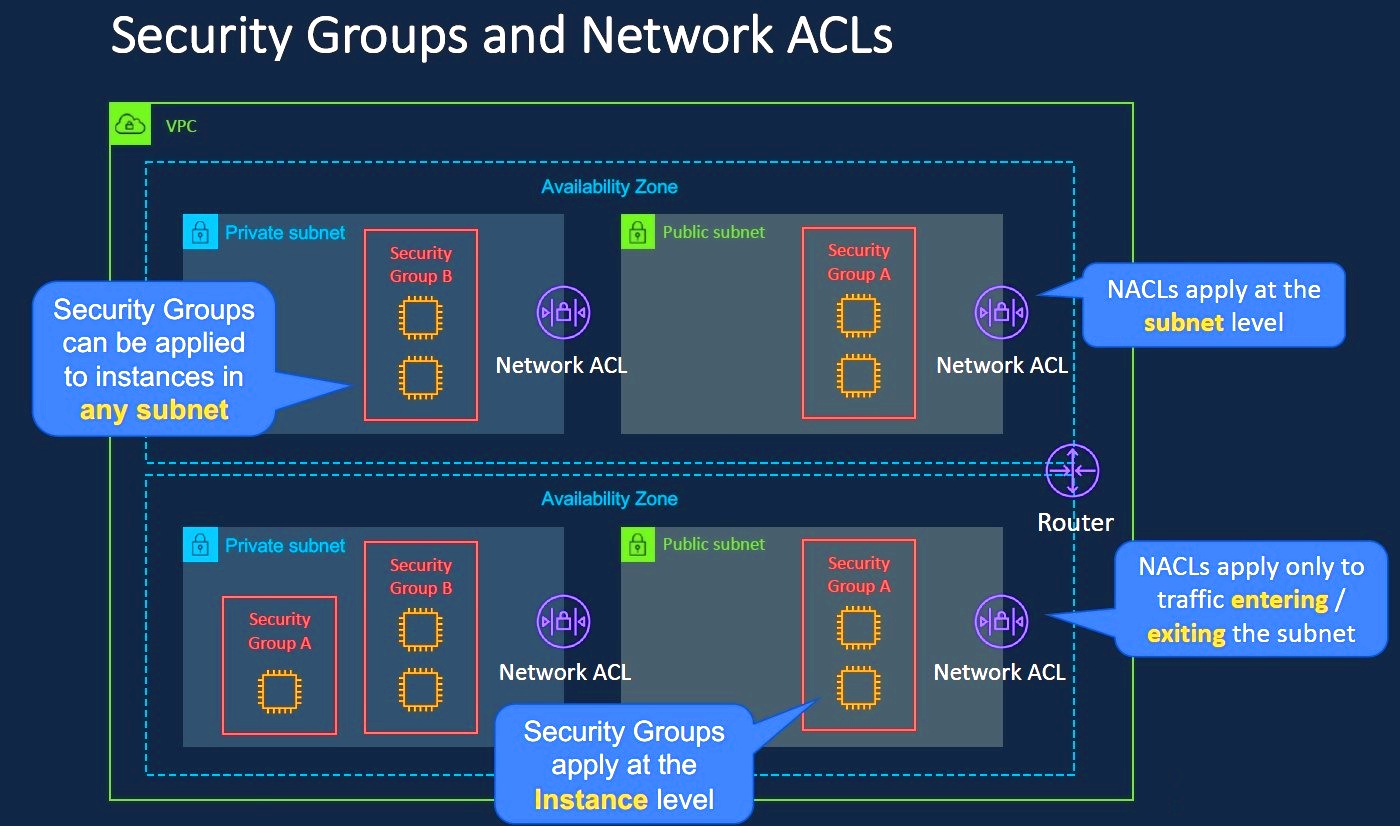
AWS Security Groups act as virtual firewalls that control inbound and outbound traffic to your EC2 instances and other resources. They operate at the instance level and can be associated with one or more instances within a VPC. Each security group contains a set of rules that determine the allowed traffic based on IP addresses, ports, and protocols.
Stateful Nature of AWS Security Groups
One of the key features of AWS Security Groups is their statefulness. This means that if you allow inbound traffic from a specific source, the response traffic is automatically allowed, even if there is no explicit outbound rule for that traffic. This stateful behavior simplifies rule management and enhances security.
How Stateful Filtering Works
When a request is made to an EC2 instance, the security group examines the inbound rules. If the request is allowed, the security group tracks the connection and permits the corresponding outbound response traffic, regardless of outbound rules. This stateful nature ensures that return traffic is automatically allowed, reducing the need for complex rule configurations.
Stateful vs Stateless
Unlike AWS Security Groups, network ACLs (Access Control Lists) in AWS are stateless. This means you need to explicitly allow both inbound and outbound traffic in the network ACL rules. The stateful nature of security groups provides more straightforward rule management compared to the stateless nature of network ACLs.
Creating AWS Security Groups
Creating and configuring AWS Security Groups is straightforward using the AWS Management Console, CLI, or SDKs. Here’s a basic example of how to create a security group using the AWS Management Console:
Step-by-Step Guide
- Sign in to the AWS Management Console.
- Navigate to the EC2 Dashboard and select Security Groups from the left-hand menu.
- Click the Create Security Group button.
- Provide a name and description for the security group, and select the VPC where you want to create it.
- Define inbound and outbound rules. For example, you can add a rule to allow HTTP traffic (port 80) from anywhere (0.0.0.0/0).
- Review your settings and click Create Security Group.
Example Using AWS CLI
aws ec2 create-security-group --group-name MySecurityGroup --description "My security group" --vpc-id vpc-12345678
The above command creates a new security group with the specified name and description in the provided VPC. To add rules, you can use the authorize-security-group-ingress and authorize-security-group-egress commands.
Examples of Stateful Rules
Here are some common scenarios illustrating how AWS Security Groups handle stateful rules:
Allowing HTTP and SSH Traffic
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:AuthorizeSecurityGroupIngress",
"Resource": "arn:aws:ec2:region:account-id:security-group/sg-id",
"Condition": {
"IpAddress": {
"aws:SourceIp": "0.0.0.0/0"
}
}
},
{
"Effect": "Allow",
"Action": "ec2:AuthorizeSecurityGroupIngress",
"Resource": "arn:aws:ec2:region:account-id:security-group/sg-id",
"Condition": {
"IpAddress": {
"aws:SourceIp": "0.0.0.0/0"
}
}
}
]
}
In this example, HTTP (port 80) and SSH (port 22) traffic are allowed from anywhere. The stateful nature means that if an HTTP request is allowed, the corresponding response is also allowed automatically.
Restricting Access by IP
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:AuthorizeSecurityGroupIngress",
"Resource": "arn:aws:ec2:region:account-id:security-group/sg-id",
"Condition": {
"IpAddress": {
"aws:SourceIp": "192.168.1.1/32"
}
}
}
]
}
This example allows traffic only from a specific IP address. The stateful property ensures that responses to this traffic are also automatically permitted.
Best Practices
To ensure effective security management using AWS Security Groups, consider the following best practices:
- Use Least Privilege Principle: Define rules that allow only the minimum necessary traffic.
- Regularly Review and Update Rules: Periodically review security group rules to ensure they meet current security requirements.
- Leverage Multiple Security Groups: Use multiple security groups to apply different rules to different resources for better segregation.
- Monitor Security Group Changes: Enable logging and monitoring to track changes and access patterns for security auditing.
Troubleshooting Common Issues
If you encounter issues with AWS Security Groups, here are some common troubleshooting steps:
1. Access Issues
Ensure that inbound and outbound rules are correctly configured and that the source/destination IP addresses and ports are accurate.
2. Unexpected Traffic Blocks
Check for conflicting rules in multiple security groups or network ACLs that might be affecting traffic.
3. Security Group Limits
Verify that you haven’t exceeded the limits for security groups or rules within your VPC.
Conclusion
AWS Security Groups are a fundamental component of AWS network security, offering stateful filtering to
simplify rule management and enhance protection. By understanding their stateful nature and applying best
practices, you can effectively manage and secure your AWS resources.
Related content